“Right ear specialist and left ear specialist". No, this isn't a comedy sketch - it's a telling joke from Atul Gawande's 'The Checklist Manifesto' about super specialization in the medical field. When experts become too specialized, they lose sight of the whole system. Sound familiar? Welcome to cybersecurity in 2025.
Our industry is fractured into dozens of disconnected specialties. Network security, endpoint protection, email defense, cloud security - each operating in its silo. No context. No connection. No big picture. Like the ear specialists, each tool examines its narrow slice while missing the complete attack story.
Here's the reality: We design defenses as if attackers will politely use one vector at a time - maybe phishing today, a vulnerability exploit tomorrow. But attackers don't play by these rules. They hit everything simultaneously. Yet our defenses remain stubbornly siloed.
The industry's answer? SIEM and SOAR platforms - expensive bandaids on a fragmented security stack. The result? An avalanche of disconnected alerts overwhelms security teams. Consider this: email - the number one vector for malware and ransomware - still lives in its world, separate from the endpoint and network defense.
Here's a curious pattern: None of the significant endpoint companies have ventured into email security. Network security vendors haven't expanded into endpoint protection. Email security companies haven't built endpoint capabilities. It's as if these attack vectors exist in parallel universes. Microsoft is the lone exception, combining email security with Defender - but they're the outlier, not the norm.
But what if we're asking the wrong question? What if the solution isn't about integrating applications but eliminating them entirely?
This is where Satya’s vision becomes revolutionary. He sees a future where applications themselves vanish, replaced by AI agents that interact directly with data and systems. No more intermediaries. No more silos. No more fragmentation.
Microsoft's Copilot offers a glimpse of this future - where complex security operations become intuitive conversations, where artificial intelligence bridges the gaps between our fragmented defenses. In cybersecurity, where we're drowning in tools and interfaces, this collapse of the traditional application layer isn't just an opportunity - it's a necessity.
The question isn't whether this transformation will happen. It's who will lead it, and who will be left behind. To understand the urgency of this transformation, we need to examine the breaking points in our current security operations.
2. The Current State of Security Operations
Today's security operations rely on a patchwork of tools—SIEM for monitoring, SOAR for orchestration, EDR for endpoints—each with its own interface and data silo. Integration is cumbersome, time-consuming, and costly.
The burden goes beyond just tool complexity. Security budgets are strained by the need to license, integrate, and maintain these tools, not to mention the resources required to train staff. Even worse, organizations struggle to find and retain the talent needed to operate this fragmented ecosystem effectively.
This traditional, tool-centric approach is unsustainable. Most tools do not interact with each other. It hampers agility, leaves gaps for adversaries to exploit, and creates operational inefficiencies. But what if we could completely reimagine this broken model? Not by prescribed by quadrants and waves, but by thinking from first principles on what customers and security teams need.
3. The Agentic Security Future
This future rests on three transformative pillars:
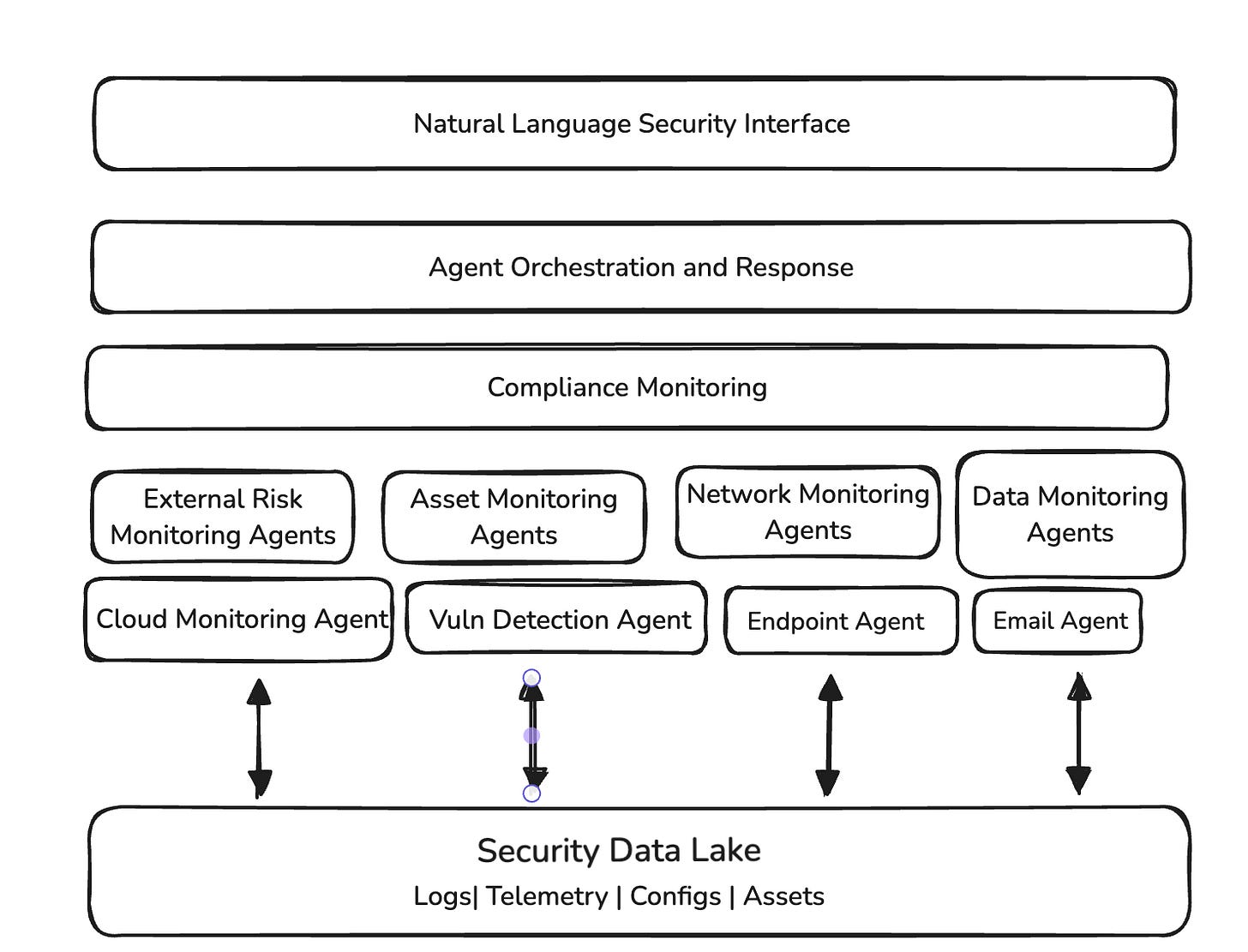
First, data, not tools, takes center stage. A unified Security Data Lake becomes the foundation, housing everything from raw logs and telemetry to configurations and asset data. AI agents interact directly with this rich data layer, eliminating the need for multiple tool interfaces. Instead of data being trapped in tool silos, it becomes a living, enriched resource that agents continuously analyze and update.
Second, natural language becomes the new command line. Through an intelligent orchestration layer, security teams interact with their entire security infrastructure through natural conversation. Imagine asking "Show me all unusual authentication attempts across our cloud services in the last hour" and getting an instant, contextual response. No more pivoting between dashboards, no more learning different query languages, no more context switching between tools. Security operations become as natural as having a conversation with an expert analyst.
Third, specialized security agents work in concert to deliver comprehensive security coverage. Each agent - whether focusing on external risks, asset monitoring, network security, or data protection - brings deep expertise to its domain. But unlike today's siloed tools, these agents share context and insights through orchestration. Cloud monitoring feeds into vulnerability detection, endpoint data enriches email security, creating a truly interconnected security ecosystem. This isn't just about integration - it's about agents actively collaborating to identify and respond to threats.
This vision isn't speculative—it's actionable. Security operations can evolve from fragmented tools to integrated, intelligent agent-driven systems.
4. Transforming Security Operations with AI Agents
The real power of this agent-based architecture becomes clear when we examine key security workflows:
Investigation becomes truly intelligent. Instead of analysts manually correlating data across multiple tools, AI agents perform automated root-cause analysis. When an alert triggers, agents instantly trace the attack path across cloud, network, endpoint, and email systems - something that would take hours or days with traditional tools.
Incident response evolves from static playbooks to dynamic action. Agents don't just follow predetermined steps - they adapt responses based on real-time threat intelligence and system state. Playbooks become living systems that learn and improve with each incident.
Threat hunting transforms from periodic searches to continuous discovery. Agents constantly analyze patterns across the security data lake, identifying subtle anomalies that traditional tools miss. They learn from each discovery, building an ever-improving threat detection capability.
Perhaps most importantly, compliance monitoring shifts from painful periodic audits to continuous assurance. Agents automatically collect and correlate evidence, track control effectiveness, and flag compliance gaps before they become issues.
The agent-driven future is compelling, but who will lead this transformation? The reality is nuanced. Startups, despite their innovation, often lack the resources to build such comprehensive systems from the ground up. Large enterprises have the resources but are frequently bogged down by existing commitments, technical debt, and incumbent solutions.
Enter the MSSPs.
5. MSSPs as the Catalyst for Change
While most MSSPs today operate with limited resources, they have a unique advantage: direct operational visibility into security challenges across multiple organizations. This multi-client perspective positions them to drive the AI agent revolution, particularly for small and medium enterprises.
The transformation path for MSSPs is practical:
From Tool Integrators to Orchestrators: Today, MSSPs struggle with managing different security tools for each client - separate endpoint solutions, different SIEM platforms, various email security tools. AI agent platforms can eliminate this complexity. Instead of managing multiple tools, MSSPs can focus on tuning agents to each client's needs.
Industry-Specific Intelligence: MSSPs often specialize in specific sectors - healthcare, finance, retail. This specialization lets them train AI agents with industry-specific attack patterns, compliance requirements, and security policies. A healthcare-focused MSSP can build agents that understand HIPAA requirements and medical device security.
Scalable Expertise: Most MSSPs hit growth ceilings due to staffing limitations. AI agents can automate routine tasks - alert triage, initial incident investigation, compliance reporting - allowing analysts to focus on high-value activities. This breaks the linear relationship between headcount and client capacity.
For MSSPs, this isn't just about technology transformation - it's about business model evolution. The question now becomes: How does this MSSP transformation reshape the broader security market? The impact creates two distinct but complementary paths forward.
6. Market Impact: SMEs and Enterprises
For SMEs, this shift makes enterprise-grade security finally accessible and affordable. Through MSSP-operated agent platforms, smaller organizations can access sophisticated security operations without building complex tool stacks or hiring specialized teams. They gain immediate access to automated threat detection, continuous compliance monitoring, and advanced threat hunting - capabilities that were previously out of reach due to cost and complexity.
Enterprises face a different challenge. With significant investments in existing security infrastructure, they need a hybrid approach that protects these investments while enabling transformation. By partnering with MSSPs, enterprises can gradually integrate AI agents alongside their legacy systems. This creates a bridge between traditional security operations and the agent-driven future, allowing for methodical transformation without disrupting critical security operations.
7. Implementation Pathways
The implementation pathway for each segment reflects these different starting points. SMEs will likely focus on selecting MSSP partners with robust agent platforms, evaluating their data isolation standards, and integration capabilities. Success metrics center on operational improvements: faster detection times, reduced alert noise, and increased automation coverage.
The MSSP agent platform architecture can evolve to support this market diversity. A scalable architecture supporting true multi-tenancy, with robust data segregation and policy enforcement, enables both SME simplicity and enterprise customization needs. Industry-specific models and compliance templates become natural differentiators in this landscape.
Enterprises can take a structured approach, starting with focused pilot projects in specific security domains like cloud security or endpoint protection. Their integration architecture addresses complex requirements through API gateways for legacy tool integration, event buses for real-time data flow, and comprehensive data connectors. A thoughtful migration framework helps sequence tool replacement while maintaining security coverage.
8. Looking Ahead: From Vision to Reality
The market evolution points toward continuous technical advancement. Agent capabilities will expand through specialized security-focused language models trained on specific security domains - from threat detection to incident response. Platforms will mature with automated deployment and resilient architectures. Standard protocols for agent communication and data sharing will naturally emerge, fostering a rich ecosystem of specialized agents and custom development frameworks.
This vision of an agent-driven security future is ambitious, and the path forward will undoubtedly be more complex than outlined here. Many technical challenges remain unsolved, from agent coordination to data privacy concerns. Yet one thing is clear: the future of security operations cannot sustain today's siloed applications and fragmented tools. The transformation from disconnected security tools to intelligent, interconnected agents isn't just desirable - it's inevitable.
As Satya noted, this shift transcends cybersecurity, representing a fundamental reimagining of how we interact with technology. The question isn't whether this transformation will happen, but how we'll shape it.
References
https://www.statista.com/chart/25247/most-common-causes-of-ransomware-attacks/





Nicely put together!!