The Korean concept of inyun (인연), beautifully captured in the film Past Lives, speaks of connections destined across time and space—relationships that must overcome obstacles before their purpose can be fulfilled. Just as the film’s characters orbit each other across decades, navigating complex paths before their shared destiny finally comes into focus, something similar is happening in federal cybersecurity.
You see, innovative startups and government agencies are like two galaxies in a cosmic dance—separated not by distance, but by an obstacle course so convoluted, it makes tax codes look like children’s books. The very compliance requirements and contracting models in place today seem like they were designed by someone who thinks dial-up internet is still cutting edge.
And while the stakes couldn't be higher, these absurd barriers keep critical innovations from reaching the very places they’re needed most: to defend our national security in an age of rapidly evolving cyber threats. But just like inyun, this partnership—between innovation and government—is destined to come together. The question is, what will it take to make it happen?
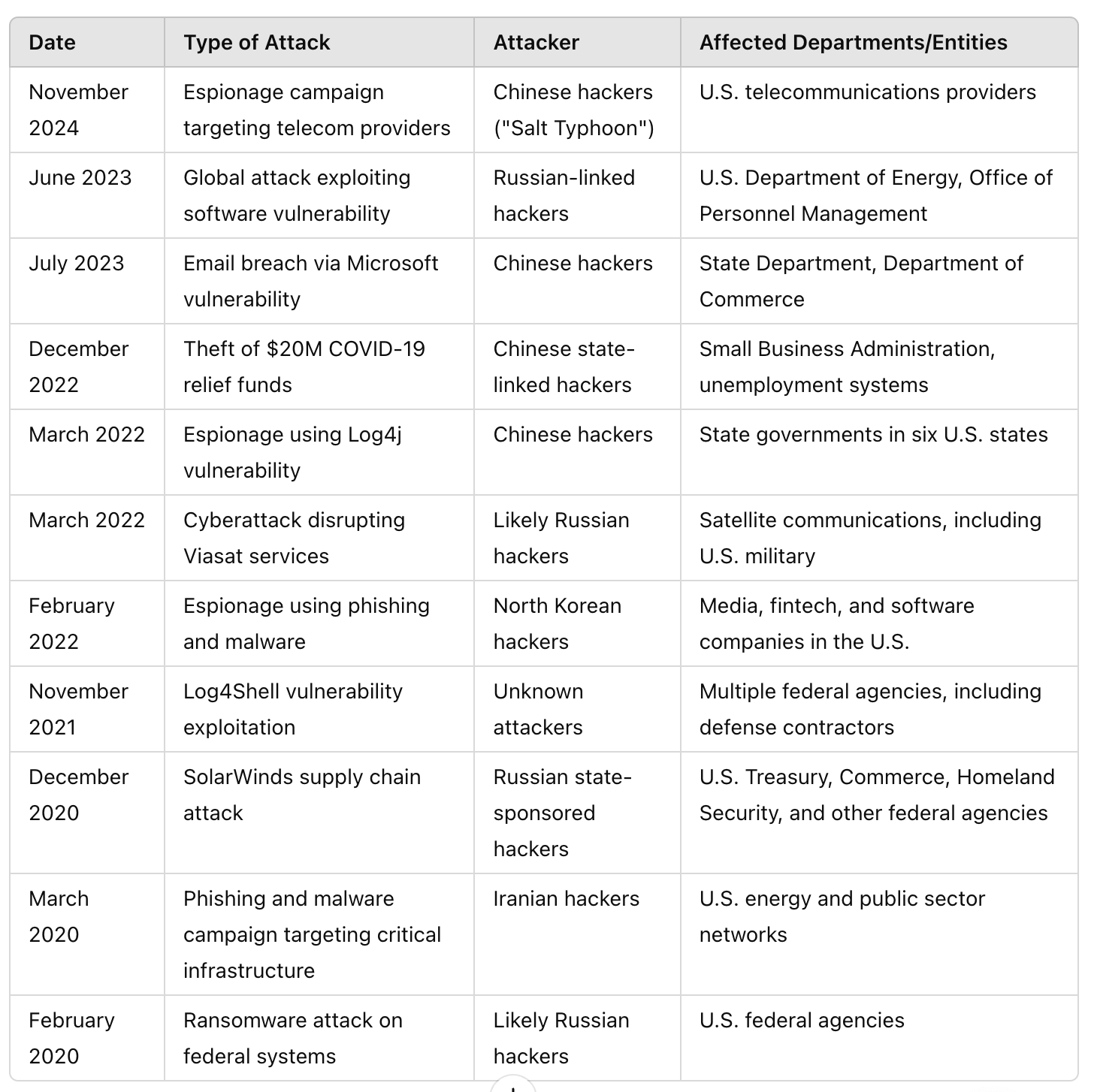
The urgency of this connection becomes clear when we examine recent history. The data paints a stark picture: from 2020-2024, state-sponsored hackers systematically probed and penetrated U.S. federal infrastructure, with the November 2024 Salt Typhoon campaign against telecom providers being the latest in this pattern. The attacks progressively targeted more critical systems - from the SolarWinds breach affecting multiple federal agencies in 2020 to the exploitation of Log4j vulnerabilities in state governments in 2022, culminating in direct assaults on telecommunications infrastructure in 2024. This escalating sophistication underscores the limitations of traditional defense contractors and procurement processes
Source: Center for Strategic & International Studies, Washington [1]
However, despite DOGE's push for efficiency, the federal cybersecurity sector remains dominated by traditional players who are ill-equipped for rapid response to evolving threats. Their extensive overhead costs, layers of management, and dated development methodologies result in solutions that are both expensive and slow to deploy. This artificial separation stems from a complex web of compliance requirements that creates high barriers to entry for startups, channeling most federal contracts to either large security corporations or specialized service providers run by veterans. Like any destined connection, the path to uniting innovative startups with federal needs requires overcoming these manufactured obstacles.
Three critical tensions define this market:
Innovation vs. Regulation: Federal agencies desperately need startup-driven innovation, yet compliance requirements effectively lock out most emerging companies.
Threat Speed vs. Response Speed: Bad actors rapidly adopt cutting-edge technologies while federal cyber defense remains constrained by slow-moving traditional contractors.
Capital Requirements: Small service providers, often founded by ex-defense contractors, lack the venture capital needed for innovation, while venture-backed startups struggle to navigate federal requirements.
These tensions create a significant opportunity for startups that can successfully bridge the gap between innovation and compliance.
Current Market Landscape
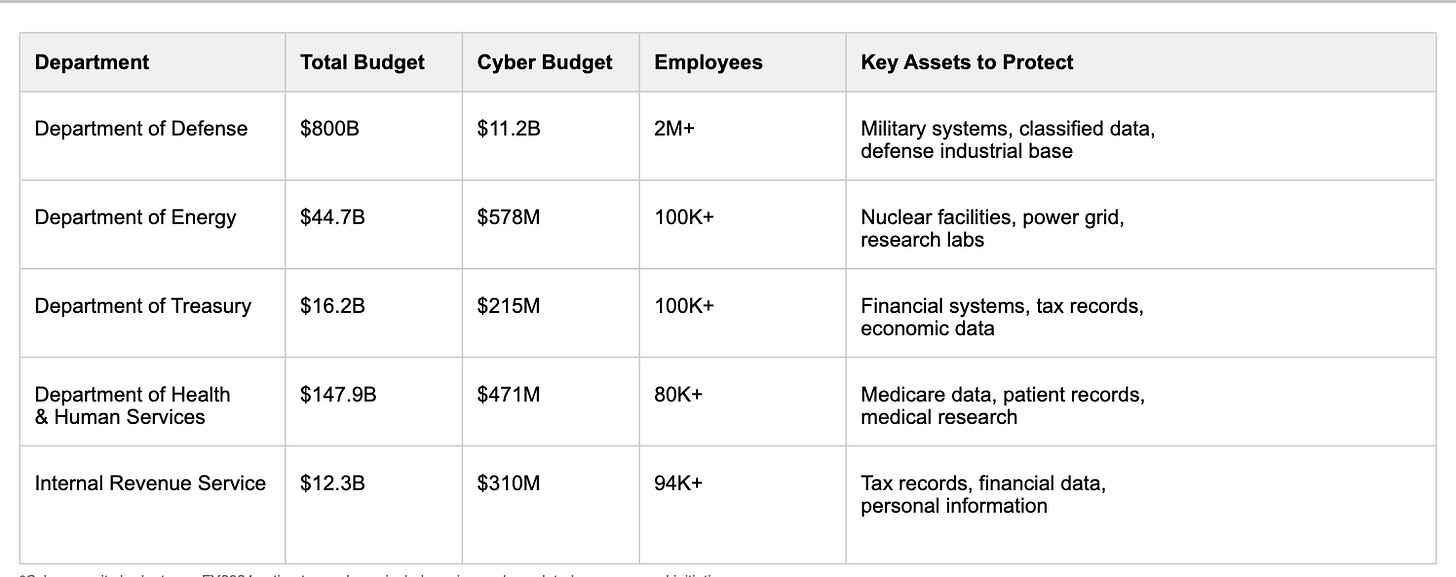
Several key federal departments require robust cybersecurity protection to safeguard our nation's most critical assets and sensitive data. Here's how these departments compare:
The Department of Defense operates at an unprecedented scale - spanning over 160 countries, managing 4,800+ sites worldwide, and commanding the largest federal budget. This makes DoD not just the largest federal organization, but one of the most complex enterprises globally.
The DoD operates through a well-established contracting system that has evolved over decades. What began as a field of 51 major defense contractors has naturally consolidated to fewer than 10 prime contractors, each bringing deep expertise in complex defense systems. In FY2022, the largest prime contractors included Lockheed Martin ($46.2B in obligations), Raytheon ($26.1B), General Dynamics ($21.6B), and Boeing ($14.8B), together handling 86% of major program spending [2]. These companies manage extensive networks of specialized subcontractors. Recent data provided by the Defense Counterintelligence and Security Agency (DCSA) estimates that covered contractors or subcontractors could number 200,000-250,000 [3].
The defense contracting landscape is far more diverse than commonly understood. An initial analysis of a subset of the DoD's contractor database provides a glimpse into this complex ecosystem. While this data only captures a portion of the defense industrial base and classification based on company names has inherent limitations, it offers interesting insights into market composition.
From this limited sample of contractors, technology firms appear to play an increasingly crucial role. While traditional defense contractors often dominate headlines, technology and IT companies represent approximately 20% of the analyzed contractors, second only to diversified suppliers in this dataset. [4]
This directional data suggests the Pentagon's growing dependence on digital infrastructure and cybersecurity. In the analyzed sample, traditional defense categories like military equipment manufacturers (2.2%) and engineering services (2.3%) show smaller representation compared to the technology sector, which includes companies providing cloud services to cybersecurity solutions.
The market structure in this sample reveals interesting patterns. Professional services firms, many of which provide compliance and security services, represent 6.5% of the analyzed contractors. The remaining ecosystem spans healthcare (1.1%), construction (1.0%), and specialized security firms (0.3%).
Most importantly, even this limited view suggests a critical trend: the defense industrial base is increasingly intertwined with the technology sector. The actual number of contractors and subcontractors is significantly larger, with estimates from the Defense Counterintelligence and Security Agency (DCSA) suggesting the total could range from 200,000-250,000 entities across the full supply chain.
This evolving composition of the defense industrial base, combined with increasing cybersecurity requirements, suggests we're at the beginning of a significant market transformation.
The Compliance Gateway: Challenge and Opportunity
This massive ecosystem of hundreds of thousands of contractors now faces an unprecedented wave of cybersecurity requirements. At the heart of this regulatory framework lies a complex web of compliance standards that every contractor must navigate – from the largest defense prime contractors to the smallest specialized manufacturers. The scope is staggering: every company in the supply chain, whether they're among the 6,000+ technology firms or part of the 2,000 professional services providers, must meet these stringent security standards.
CMMC 2.0: The New Foundation
The cornerstone of this framework is CMMC 2.0, which establishes three distinct levels of cybersecurity maturity.
At Level 1 (Foundational), organizations must implement 17 basic controls, with self-assessment costs ranging from $4,000 to $6,000 annually.
Level 2 (Advanced) significantly increases complexity with 110 controls from NIST 800-171. Companies can choose between self-assessment ($37,000–$49,000) or third-party certification ($105,000–$118,000) every three years.
Level 3 (Expert) represents the highest tier, requiring 110+ controls with NIST 800-172 enhancements. The financial impact is substantial: small entities face initial implementation costs of $2.7M, while large organizations may spend up to $4.1M. Annual recurring costs range from $490,000 for small entities to $21.1M for large organizations, with certification assessments adding $10,000–$41,000+ every three years.
NIST Framework: The Backbone
Beyond CMMC, contractors must navigate NIST 800-171 requirements across 14 control families. Implementation typically requires in-house risk assessments ($30,000–$35,000) or third-party assessments ($10,000–$15,000), plus ongoing documentation and tracking.
Cloud Services: The FedRAMP Challenge
For cloud service providers, FedRAMP certification is mandatory and demanding. The process averages 12-18 months, with initial certification costs between $500,000 and $3M. This includes 3PAO assessments ($75,000–$300,000), potential remediation (up to $200,000), and annual continuous monitoring ($50,000–$150,000).
Personnel Security: The Human Factor
Personnel security adds another layer of complexity. While the government funds clearance investigations ($420 for Secret, $5,410 for Top Secret), organizations bear significant indirect costs through facility clearances, security staffing, and training programs ($30–$700 per employee).
Continuous Monitoring: The Operational Burden
Continuous monitoring requirements further strain resources. Basic services range from $6,500 to $13,000 annually, while advanced programs can exceed $100,000. For small businesses, this creates a perfect storm: initial CMMC Level 2/3 compliance ($100,000–$2.7M), substantial annual maintenance, technical staffing ($500,000+), and potential incident response costs averaging $4.45M per breach.
The Small Business Dilemma
The complex web of compliance requirements creates a particularly challenging environment for small businesses. Basic monitoring services alone range from $6,500 to $13,000 annually, while advanced programs can exceed $100,000. When combined with initial CMMC Level 2/3 compliance costs ($100,000–$2.7M), substantial annual maintenance, and technical staffing ($500,000+), the financial burden becomes overwhelming for most small contractors.
The Small Business Trap
This financial pressure forces most small businesses into a dangerous compromise. They end up relying on basic Managed Service Providers (MSPs) that lack sophisticated security capabilities required for defense contracts. These MSPs, while affordable, create significant vulnerabilities:
Limited Security Capabilities: Basic MSPs/MSSPs typically offer standard IT services without the specialized expertise needed for defense compliance
Capital Constraints: Unable to invest in advanced security infrastructure or talent
Innovation Bottlenecks: Focus on maintaining minimum compliance rather than advancing security posture
Supply Chain Vulnerabilities: Inadequate security measures create weak points in the defense industrial base
Restricted Growth: Inability to pursue larger contracts due to compliance limitations
This creates a vicious cycle where small businesses remain trapped between inadequate security solutions and the inability to afford enterprise-grade alternatives, ultimately weakening the entire defense supply chain.
The Strategic Opportunity: Acquisition-Led Innovation
While small businesses struggle with compliance requirements and traditional MSPs fall short, this market inefficiency presents a unique opportunity for venture-backed startups. The key lies in an acquisition-first strategy that addresses both immediate compliance needs and long-term innovation potential.
Why Strategic Acquisition Makes Sense
Instant Compliance Inheritance
By acquiring established service providers, startups immediately inherit crucial compliance certifications that would otherwise take years and millions to obtain. This includes CMMC assessments, NIST attestations, and often FedRAMP authorizations – effectively bypassing the most significant barrier to market entry.
Ready-Made Contract Access
Defense contracting operates through established vehicles and relationships. Acquired companies bring:
Active contract vehicles with defense agencies
GSA Schedule listings
Subcontracting relationships with prime contractors
Past performance qualifications
Built-In Customer Base
The acquired company provides immediate access to:
Existing defense contractor relationships
Proven track record of delivery
Understanding of customer needs
Established billing relationships
Reference customers for expansion
Revenue Stability
Perhaps most crucially, this approach provides:
Steady monthly recurring revenue
Predictable government contract income
Cash flow to fund innovation
Customer relationships to test new products
Financial stability during transformation
This foundation allows venture-backed startups to focus on innovation rather than basic market access, creating a faster path to scale in the defense market. The existing business provides both the compliance framework and financial stability needed to build next-generation security solutions.
Building Competitive Moats Through Modernization
In the defense technology market, competitive advantage comes not just from having compliance, but from transforming it into a scalable, technology-driven operation. Here's how acquired MSPs can be transformed into modern security powerhouses.
The Foundation: Technology Transformation
Modernizing Legacy Infrastructure
Traditional MSPs often run on outdated technology stacks, creating an immediate opportunity for value creation. By implementing modern cloud security platforms, containerized environments, and automated security tools, acquired companies can dramatically reduce manual monitoring costs while enabling rapid deployment of security updates. This modernization enables improved threat detection capabilities and allows operations to scale without proportional headcount increases, all while maintaining standardized security baselines across the customer base.
AI-Powered Security Operations
The integration of AI transforms basic security monitoring into predictive defense. Through automated threat hunting and response systems, pattern recognition for anomaly detection, and continuous compliance monitoring, these platforms can provide sophisticated security operations that far exceed traditional MSSP capabilities. The automation extends to reporting and documentation, creating a comprehensive system that combines human expertise with machine efficiency.
Compliance Innovation
Building proprietary tools specifically for defense compliance creates another layer of competitive advantage. Real-time CMMC compliance monitoring and automated NIST control validation systems provide continuous security scoring that was previously impossible with manual processes. This automation of compliance workflows and integrated audit trail generation transforms what was once a periodic assessment into continuous compliance assurance.
The Multiplier: Scaling Advantages
Relationship Leverage
Existing relationships provide the foundation for growth through natural expansion opportunities. As customers see the value of enhanced security services and new compliance tools, upselling becomes organic rather than forced. The ability to expand within current accounts while using successful deployments as references for new business significantly reduces customer acquisition costs.
Network Effects
Perhaps most importantly, each new customer strengthens the overall security platform through network effects. Shared threat intelligence across the customer base improves detection capabilities through a broader data set. Common compliance frameworks and collective defense capabilities create an ecosystem of security partnerships that becomes increasingly valuable as it grows.
Data Moats
The continuous monitoring of security events creates valuable data assets that further strengthen competitive positioning. Through threat pattern recognition and compliance benchmark data, the platform develops increasingly sophisticated risk assessment models. This accumulation of industry-specific security insights creates a data moat that becomes deeper and more valuable over time.
The Investment Case: Why Federal Tech MSPs/MSSPs Present a Unique Opportunity
Market Dynamics: A Perfect Storm
The defense and federal technology market is experiencing unprecedented transformation. The Department of Defense alone plans to spend $11.2B on cybersecurity in FY24, and this is just part of the broader federal cybersecurity landscape.
The broader cybersecurity services market presents an even more compelling opportunity. The enterprise security services market will have a CAGR of 12.3%, growing from $73.9 billion to $116.8 billion by 2028 [6]. While federal contracts provide a stable foundation, modernized security platforms can serve both government and commercial clients, significantly expanding the total addressable market.
This market opportunity extends well beyond direct federal spending. The extensive network of contractors and subcontractors supporting these agencies must all meet stringent cybersecurity requirements, creating a multiplier effect. From the Department of Energy's national laboratories to NASA's space programs, and from the Department of Homeland Security's critical infrastructure protection to the intelligence community's classified networks, each domain requires specialized cybersecurity solutions. Moreover, startups entering this space can leverage their federal compliance credentials to win enterprise customers who increasingly seek government-grade security solutions.
The CMMC 2.0 Timeline: A Market Catalyst
The Department of Defense's CMMC 2.0 program officially went into effect in December 2024 [5], marking the beginning of a structured four-year implementation journey that will reshape the defense industrial base's cybersecurity landscape.
Phased Implementation
The rollout follows a carefully planned sequence. Beginning in early 2025, new contracts started incorporating Level 1 and Level 2 self-assessment requirements. By 2026, the program will intensify as third-party assessments become mandatory for Level 2 certification. The requirements continue to escalate through 2027 with Level 3 DIBCAC assessments, culminating in full implementation across all applicable contracts by 2028.
Most critically, all new DoD contracts must include CMMC compliance mandates by October 1, 2026. This creates a clear timeline for market transformation and presents an immediate opportunity for investors and startups to position themselves ahead of this mandatory requirement.
This phased approach provides a predictable timeline for market evolution while creating urgency for contractors to begin their compliance journey. For venture investors, this structured rollout offers a clear window to execute acquisition and transformation strategies before the market consolidates.
Value Creation Levers: Multiple Paths to Returns
The transformation opportunity in security MSPs offers several compelling value creation mechanisms across both federal and commercial markets. At the core is revenue transformation through technology – replacing manual processes with automated solutions that can scale efficiently across multiple customer segments. Early movers have demonstrated the ability to double or triple revenue within 24 months of modernization while significantly improving margins through multi-market expansion.
Margin expansion through automation becomes even more powerful when applied across diverse customer bases. Traditional MSPs typically operate at 15-20% EBITDA margins, but modernized platforms can achieve 30-40% margins through AI-driven operations and reduced human dependencies. This improvement in unit economics enables competitive pricing in the federal space while maintaining premium pricing in commercial markets.
The opportunity for multiple arbitrage is particularly compelling in a dual-market strategy. While traditional MSPs trade at 4-7x EBIDTA, modernized security platforms with recurring revenue and strong growth across federal and commercial markets can command 15-20x+ multiples. This creates significant value through both operational improvements and multiple expansion.
Why Now: Market Convergence
The implementation of CMMC 2.0 coincides with increasing commercial demand for government-grade security solutions. As hundreds of thousands of contractors face new compliance requirements, and enterprises seek stronger security frameworks, the market is entering a unique phase where federal compliance capabilities become a competitive advantage in commercial markets.
The path to building significant businesses is clear. With the right execution, transformed MSPs can reach $100M+ in ARR by capturing even a small fraction of both federal and commercial markets. The combination of recurring revenue, high margins, and strong barriers to entry creates highly defensible market positions across multiple sectors.
The Call to Action
For venture investors like David Sacks, this represents a rare opportunity to reshape critical markets while generating exceptional returns. The convergence of federal and commercial security needs offers:
Structural Advantages
The combination of federal compliance capabilities and commercial market opportunities creates natural moats that protect returns once established. Federal past performance credentials become powerful marketing tools for commercial enterprise sales.
Clear Exit Paths
Multiple exit options exist through:
Strategic acquisitions by large technology or defense contractors
Private equity roll-ups as the market consolidates
Potential public markets exits as platform scale increases across sectors
Timing Opportunity
The convergence of CMMC 2.0 implementation and increasing commercial demand for government-grade security creates a unique market timing opportunity. Early movers who can execute on the MSP acquisition and transformation strategy now will establish dominant positions across both federal and commercial markets.
The security technology market stands at an inflection point where federal compliance requirements, commercial security needs, and technological transformation align to create exceptional investment opportunities. For venture investors willing to execute on this strategy, the potential for both financial returns and market impact is compelling across multiple sectors.
Conclusion
The federal cybersecurity market stands at a transformative moment. The barriers between innovation and national security are finally breaking down, driven by urgent needs and regulatory change.
The path forward is clear:
A massive $14.1B federal cybersecurity market that's actively seeking innovation
A fragmented landscape of 200,000+ contractors requiring modernization
A clear regulatory timeline through CMMC 2.0 creating urgency
The ability to leverage federal compliance as a competitive advantage in commercial markets
The acquisition-led strategy we've outlined offers more than just market entry – it provides the means to bridge these worlds. By acquiring and modernizing MSPs serving the defense industrial base, we can transform compliance from a barrier into an accelerator of innovation.
David Sacks's leadership in shaping government's approach to AI and cryptocurrency regulation demonstrates the impact of bringing sharp technological insight to regulatory challenges. His ability to navigate complex regulatory frameworks while driving innovation makes him uniquely positioned to help bridge the cybersecurity divide. The federal security sector needs this same level of thoughtful leadership to navigate its transformation.
The security of our digital infrastructure cannot wait. The technology exists, the market is ready, and the opportunity to reshape federal cybersecurity is now.
References
[2] https://sgp.fas.org/crs/natsec/IF10600.pdf
[4]https://dodsoco.ogc.osd.mil/Portals/102/Documents/Conflicts/2024%2025K%20FY2023.pdf
[5]https://www.ridgeit.com/what-is-cmmc-compliance-deadline-2025-guide/
[6] https://www.gartner.com/en/articles/information-security#:~:text=Information%20security%20market%20growth%20by%20subsegment&text=The%20enterprise%20security%20software%20market,with%20a%20CAGR%20of%2010.6%25