Security Automation's Blind Spot: Analysis of 10,000 Jobs Shows We're Solving the Wrong Problems
Subtitle: 10,000 Job Postings Show We're Just Making Box 3.0 When We Need Middle-Out
[For the uninitiated: The title references HBO's Silicon Valley, where Pied Piper's revolutionary "middle-out compression" challenged traditional "Box" storage solutions - much like today's security automation challenges.]
Ever feel like you're in a Gavin Belson presentation trying to decode why "the bear is sticky with honey"? In today's security landscape, we're bombarded with pseudo-profound statements about AI and automation revolutionizing cybersecurity. We vendors promise seamless integration, intelligent automation, and AI-powered everything – but what's actually happening on the ground?
To cut through the buzzwords and understand what security teams really need, we analyzed over 10,000 security job postings across the industry. The results tell a fascinating story about the gap between automation promises and operational reality.
Our analysis, while comprehensive, comes with an important caveat: job descriptions often suffer from "requirement inflation," where organizations list every conceivable skill or technology rather than focusing on core necessities. Many job postings are created using templates or copied from similar positions, leading to overlapping or unrealistic requirements. Therefore, while our findings provide valuable insights into market trends and employer expectations, they should be viewed as indicators rather than definitive statements about the actual skills needed to perform these roles effectively.
This analysis includes examining 17 security roles. This is a multi-part blog. In part 1 we're starting with the focus on foundational security roles (Security Consultants, SOC Analysts, Security Analysts, Security Specialists, Security Engineers, and Security Operations Engineers) due to their generalist nature in cybersecurity operations. Unlike specialized positions such as Penetration Testing Engineer or Cloud Security Engineer, these roles often have overlapping responsibilities and interchangeable titles across organizations. By analyzing these broader roles first, we can establish baseline trends in the security job market before examining more specialized positions with clearly defined scopes and requirements.
Security Consultants
SOC Analysts
Security Analysts
Security Specialists
Security Engineers
Security Operations Engineers
Our deep dive into 4,456 positions across these roles reveals surprising patterns about how organizations are actually approaching security automation. While vendors talk about no-code solutions and AI-driven platforms, the job market tells a different story – one where programming skills are more in demand than the tools they're supposed to automate.
Let's look at what the data tells us about the real state of security automation.
Role Analysis: The Foundation of Security Operations
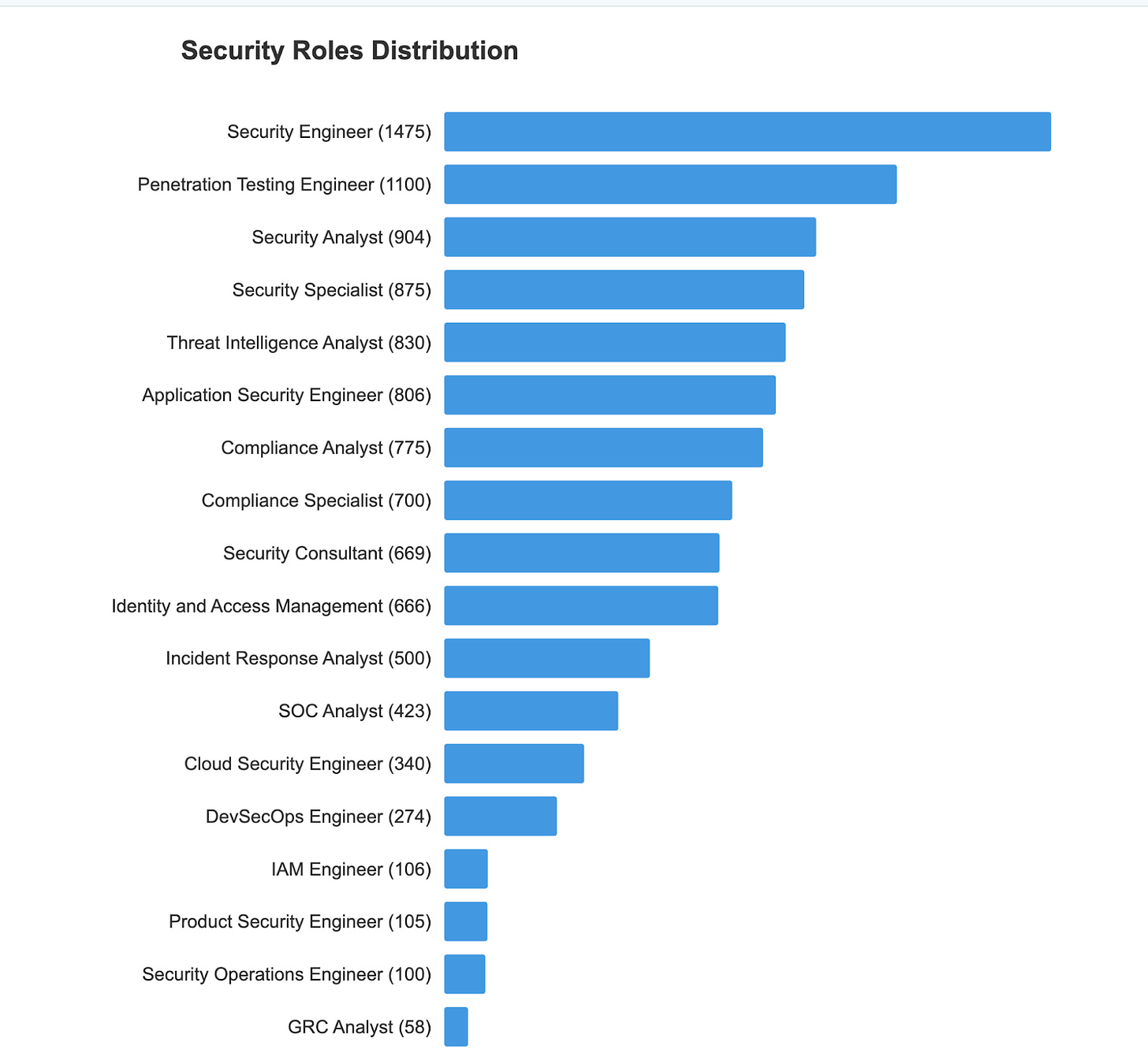
Our analysis of 4,456 positions across Security Consultants, SOC Analysts, Security Analysts, Security Specialists, Security Engineers, and Security Operations Engineers reveals interesting patterns about how organizations structure their security operations.
Security Engineers and Security Analysts emerge as the most in-demand roles, with approximately 875 and 904 positions, respectively. These core technical roles form the backbone of security operations, responsible for both building security infrastructure and analyzing security data. Security Specialists follow closely behind, suggesting organizations need versatile security professionals who can adapt to various security domains.
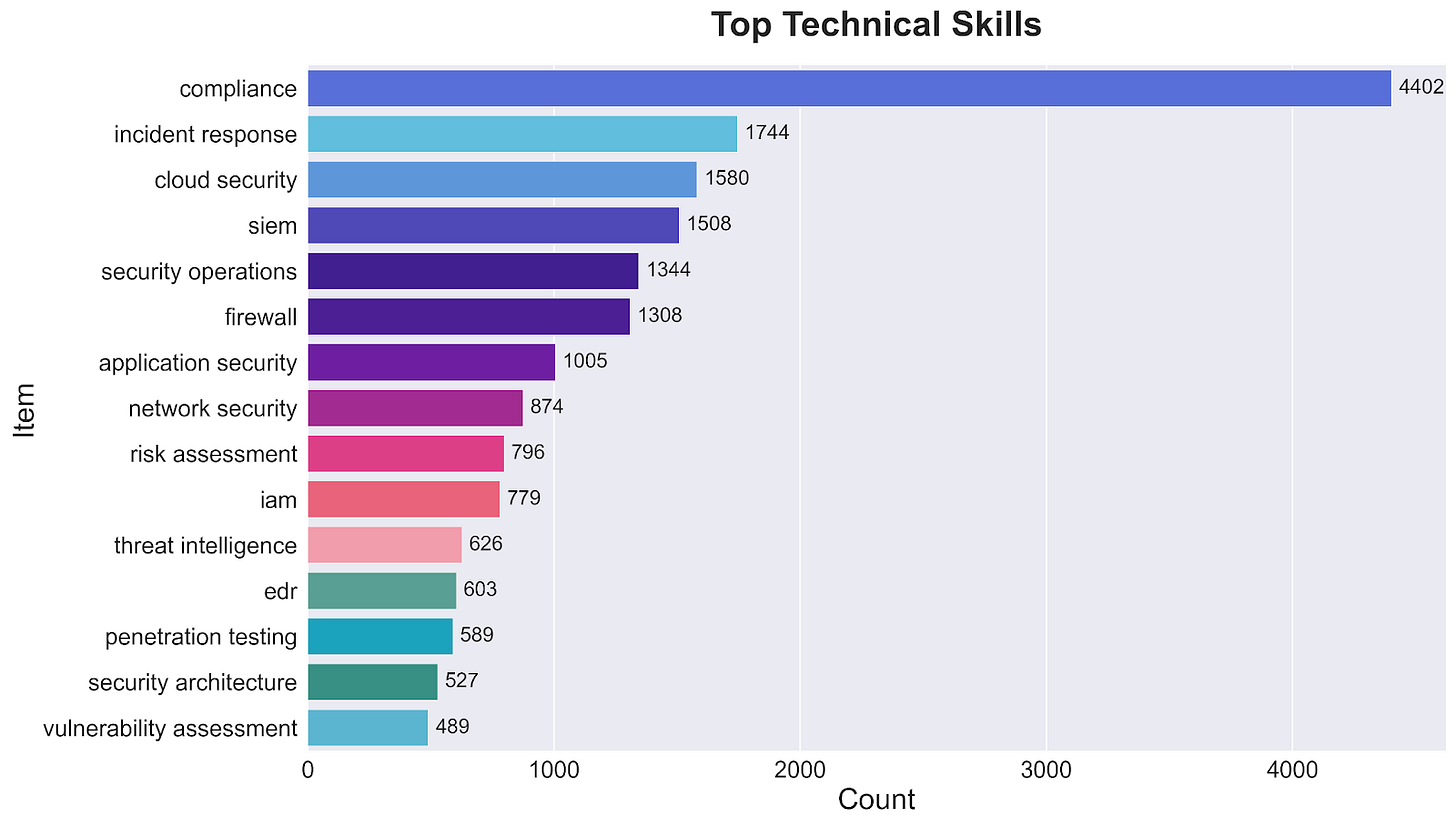
The Technical Skills Reality: Compliance Leads, Security Follows
In our analysis of security job postings, technical skill requirements paint an unexpected picture. While security operations and cloud expertise might seem like natural priorities, compliance dominates with 4,402 mentions - more than double any other skill requirement.
The next tier of demanded skills reveals today's operational focus:
Incident response (1,744 mentions)
Cloud security (1,580 mentions)
SIEM expertise (1,508 mentions)
Security operations (1,344 mentions)
Firewall skills (1,308 mentions)
Traditional defensive skills make up 42% of all mentions, increasingly paired with specialized capabilities like cloud and application security. Meanwhile, advanced security skills like penetration testing (589 mentions) and security architecture (527 mentions) appear less frequently, suggesting organizations prioritize day-to-day operations and compliance over specialized security functions.
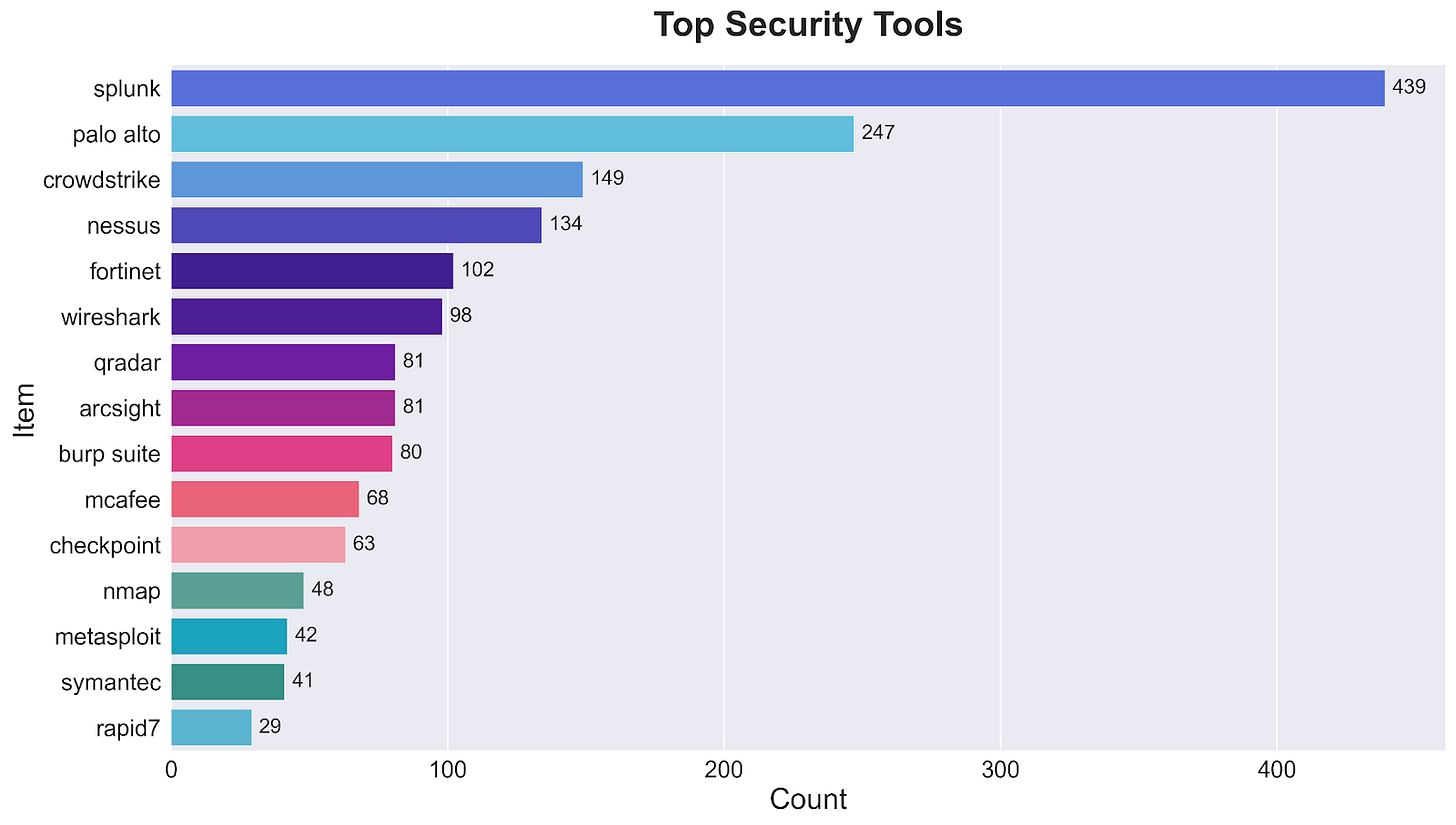
The Security Tools Reality: More Tools, More Integration Needs
The security tools landscape reveals an interesting hierarchy of what organizations are actually using. SIEM platforms lead the pack, with Splunk dominating at 439 mentions. This suggests that despite years of automation promises, organizations still heavily rely on centralized logging and monitoring.
Network security tools follow, with Palo Alto (247 mentions) and Fortinet (102 mentions) showing strong presence. The emergence of next-gen endpoint solutions is clear with CrowdStrike at 149 mentions, while traditional players like McAfee (68 mentions) and Symantec (41 mentions) show lower demand.
What's particularly telling is the mix of monitoring and assessment tools. While Splunk leads overall, vulnerability scanners like Nessus (134 mentions) and penetration testing tools like Burp Suite (80 mentions) and Metasploit (42 mentions) indicate organizations are building both defensive and offensive capabilities.
The relatively modest numbers across all tools - even the leader Splunk only appears in about 10% of postings - suggests that security teams need to work with multiple tools rather than standardizing on a single platform. This helps explain the high demand for programming skills we saw earlier - someone needs to make all these tools work together.
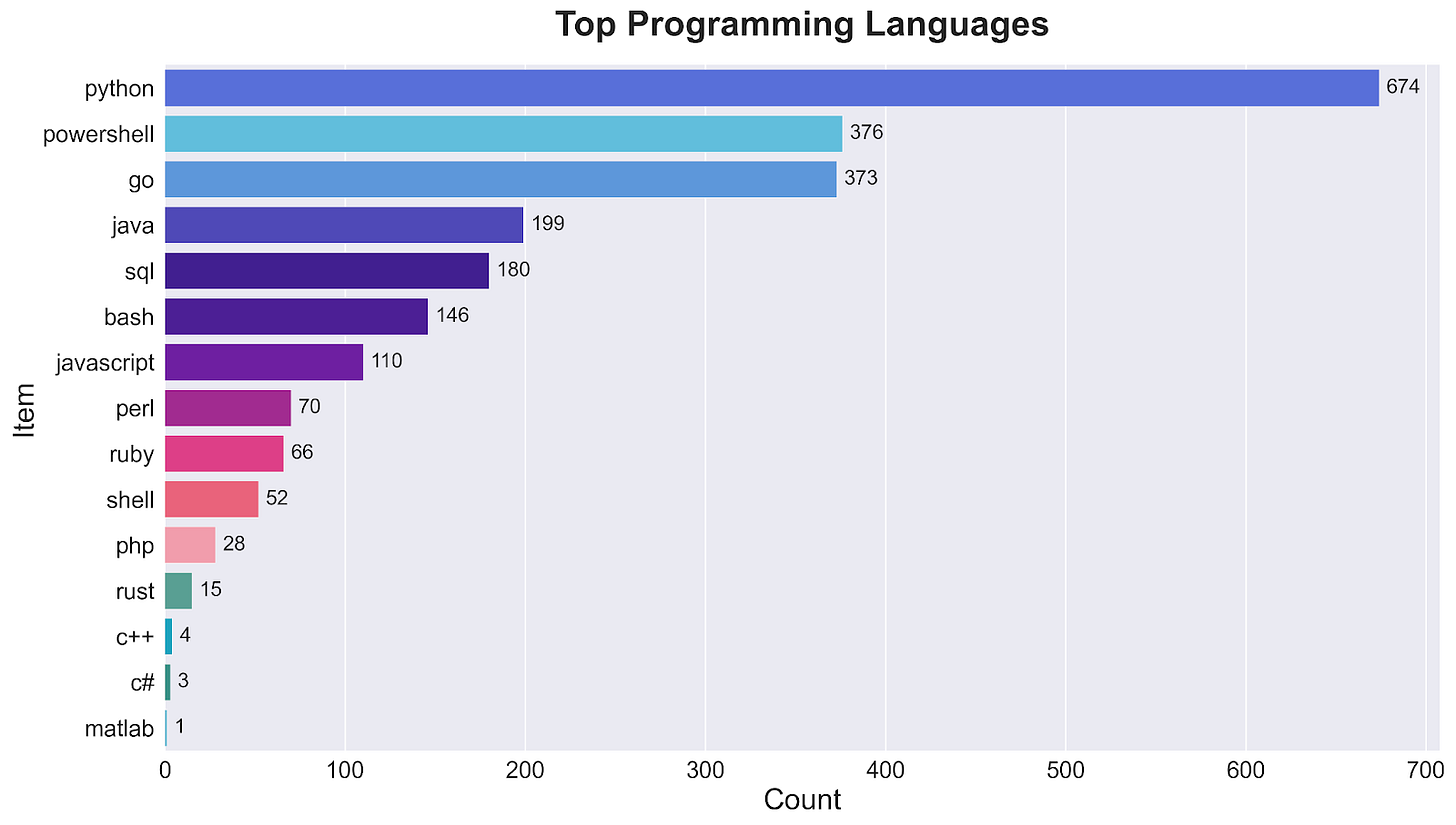
The Programming Paradox: When Security Means Software
In an era of "no-code" automation and SOAR platforms, programming languages appear with surprising frequency in security job postings. The distribution tells an interesting story about how security teams are actually implementing automation.
Python dominates with 674 mentions, accounting for nearly 30% of all programming language requirements. This isn't surprising given Python's strong security and automation libraries, but the scale of demand suggests teams are building substantial custom solutions.
What's more telling is the strong showing of PowerShell (376 mentions) and Go (373 mentions), nearly tied for second place. This indicates security automation spans both Windows environments and modern microservices architectures. Traditional enterprise languages like Java (199 mentions) and SQL (180 mentions) round out the top five.
The long tail of languages - from Bash to Rust - suggests security teams aren't just scripting simple tasks; they're building complex applications and integrations. The presence of systems programming languages like Go and Rust hints at teams developing high-performance security tools rather than just automation scripts.
This diversity of programming languages, appearing more frequently than many security tools, suggests that despite vendors' promises of comprehensive automation solutions, organizations are still writing significant custom code to make their security tools and processes work together.
Further, analysis of cybersecurity job requirements exposes a striking irony in security automation trends. While SOAR (Security Orchestration, Automation, and Response) platforms are marketed as solutions to simplify and automate security operations, the job market reveals an unexpected twist. SOAR-related positions demand significantly higher programming expertise across multiple languages compared to traditional security roles, with Python skills being especially crucial (29% vs 16% in other security jobs). This counterintuitive pattern suggests that rather than reducing the need for coding expertise, SOAR platforms are spawning a new breed of "automation engineers" who require even deeper programming knowledge. The substantial demand for PowerShell (22%) and other scripting languages reflects a reality where organizations heavily rely on custom code to bridge gaps between systems, handle edge cases, and create specialized integrations. This disconnect between the promise of simplified automation and the growing demand for advanced programming skills highlights a critical gap in current SOAR solutions.
Beyond Spreadsheets and Checklists: The Drive to Automate Compliance
The data tells a compelling story. A substantial 71.2% of analyzed positions (2,506 jobs) explicitly mention compliance requirements, highlighting its critical role in modern security operations. More tellingly, among these compliance-focused positions, nearly two-thirds (63.9%) specifically mention automation, signaling a clear organizational push to move away from manual compliance processes.
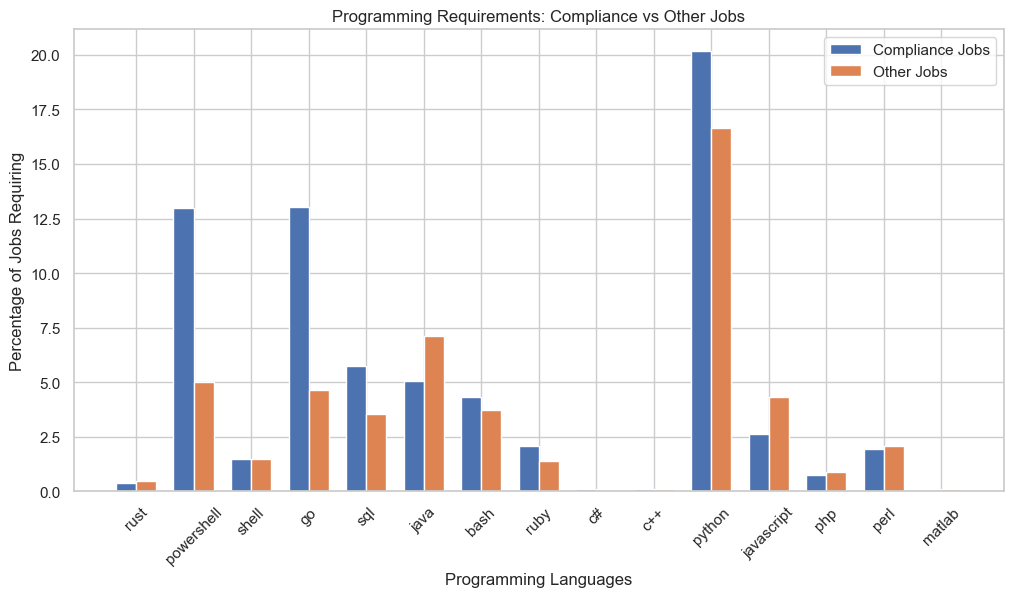
This shift towards automation is further reflected in the programming requirements for compliance-focused roles. Python leads the pack at 20.2%, followed by Go and PowerShell, each at 13.0%. The emphasis on these particular languages is significant when compared to non-compliance roles:
Python: 20.2% vs 16.7% in non-compliance roles
Go: 13.0% vs 4.6%
PowerShell: 13.0% vs 5.0%
SQL: 5.7% vs 3.6%
What makes these numbers particularly revealing is the nature of the required programming languages. Python and PowerShell are widely recognized for their automation capabilities, while Go's significant presence (13.0%) suggests companies are investing in building robust, scalable compliance automation tools. The higher SQL requirements point to a focus on automating compliance reporting and data analysis.
These findings paint a clear picture: organizations are no longer content with manual compliance processes. The consistent emphasis on programming skills across compliance roles, combined with the explicit mention of automation in job descriptions, indicates a strategic shift towards automating compliance workflows. This trend suggests companies are actively working to transform compliance from a manual burden into a more efficient, automated process.
The Collaboration Stack: Security Doesn't Work in Silos
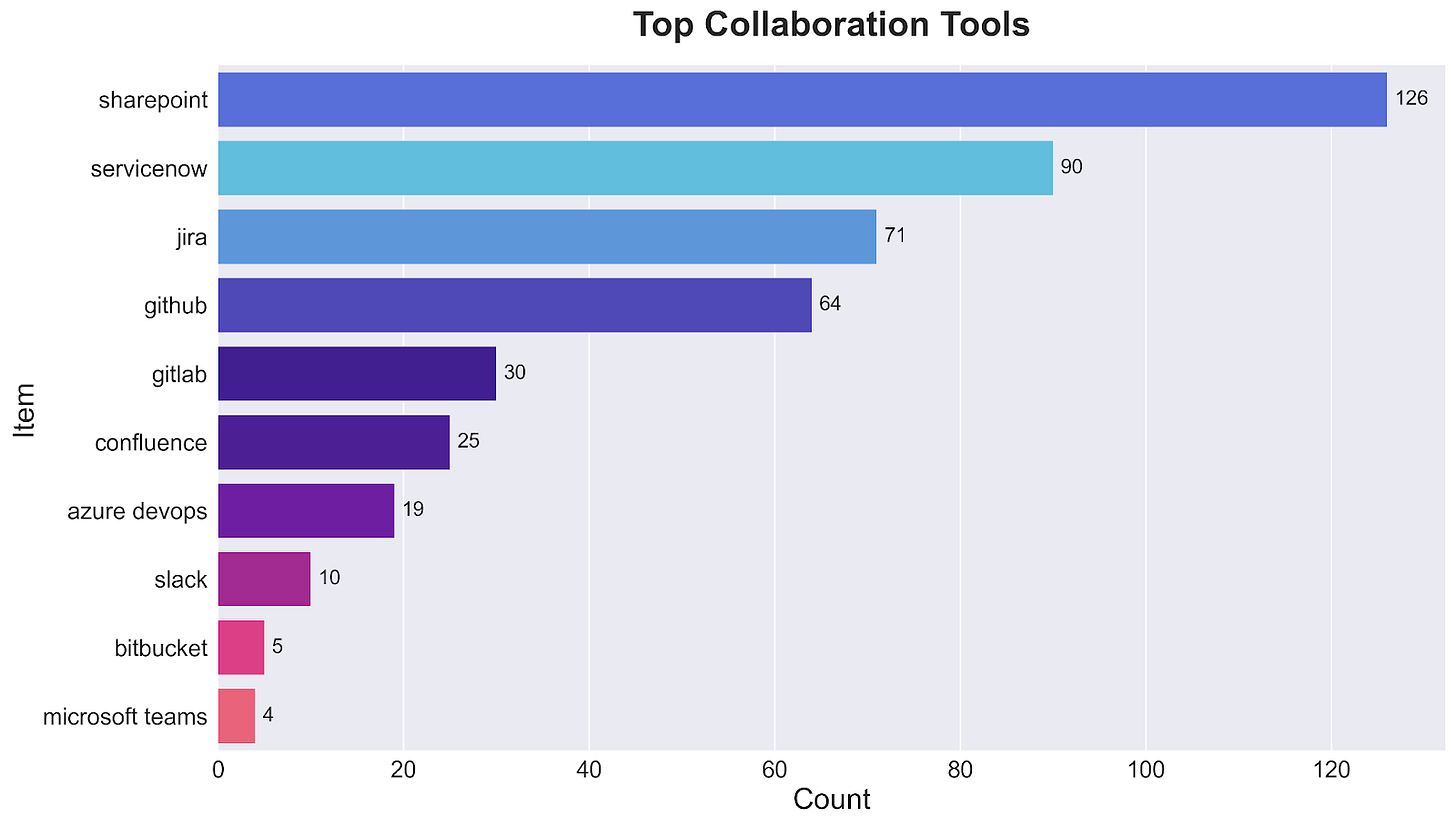
The collaboration tools appearing in security job postings reveal how security automation fits into broader organizational workflows. SharePoint leads with 126 mentions, but it's ServiceNow (90 mentions) and Jira (71 mentions) that tell the more interesting story about security automation.
The strong presence of ticketing and workflow platforms (ServiceNow, Jira) suggests security automation isn't just about detecting and responding to threats - it's about managing security processes across teams. Meanwhile, the significant showing of development platforms like GitHub (64 mentions) and GitLab (30 mentions) indicates security teams are adopting software development practices for their automation efforts.
What's particularly telling is that traditional communication tools like Slack (10 mentions) and Microsoft Teams (4 mentions) appear less frequently than development and process management tools. This suggests security automation is more focused on structured workflows and code management than on real-time communication.
The Compliance Reality: When Standards Drive Security
Analysis of over 4,000 compliance framework mentions across security job postings reveals how regulations are shaping security automation. NIST frameworks dominate with 1,474 mentions - not just in government contracts, but across sectors. The framework's expansion beyond its federal origins tells an interesting story about modern security practices.
Defense contractors like Northrop Grumman and Leidos show consistent NIST requirements, as expected. But it's the adoption by financial services (Capital One), consulting giants (Deloitte, EY), and retailers (Target) that shows how NIST has become a de facto standard. Even when not legally required, organizations are choosing NIST as their security baseline.
Healthcare follows closely with HIPAA (1,011 mentions), while financial services add layers of PCI DSS (392 mentions) and SOX (233 mentions) requirements. International business brings its own complexity with GDPR (250 mentions) and ISO 27001 (394 mentions). Newer regulations like CCPA (54 mentions) and CMMC (57 mentions) are already appearing in job requirements, suggesting security automation needs to be adaptable to evolving compliance landscapes.
What's telling is that many positions require knowledge of multiple frameworks - suggesting that security automation isn't just about efficiency, it's about consistently proving compliance across overlapping requirements. When a single security position might need to handle four or five different frameworks, automation becomes less about choice and more about necessity.
The Experience Equation: What Security Teams Actually Need
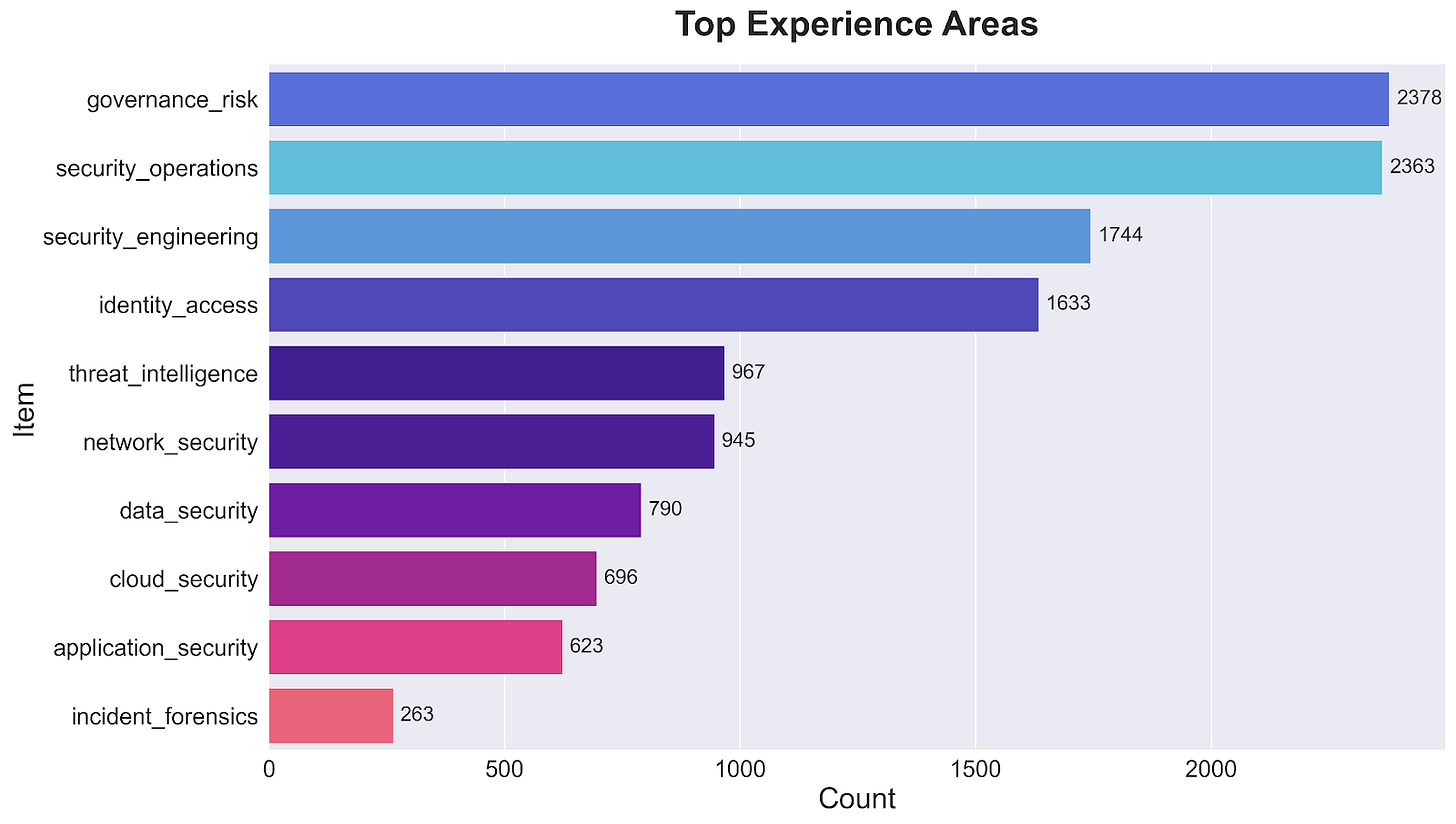
Analysis of 12,402 experience requirements reveals an almost even split at the top: Governance & Risk (2,378 mentions) and Security Operations (2,363 mentions) lead the demands. This parity suggests security teams need both operational capability and risk management expertise.
The next tier shows the technical foundation:
Security Engineering: 1,744 mentions
Identity & Access Management: 1,633 mentions
Threat Intelligence: 967 mentions
Network Security: 945 mentions
Specialized areas follow with notably lower demand:
Data Security: 790 mentions
Cloud Security: 696 mentions
Application Security: 623 mentions
Incident Forensics: 263 mentions
This distribution suggests organizations prioritize broad security management capabilities over specialized technical skills. The high demand for governance experience, coupled with earlier findings about compliance requirements, indicates security teams need people who can build automated solutions that satisfy both operational and regulatory needs.
The Certification Priority: Governance Leads, Technical Follows
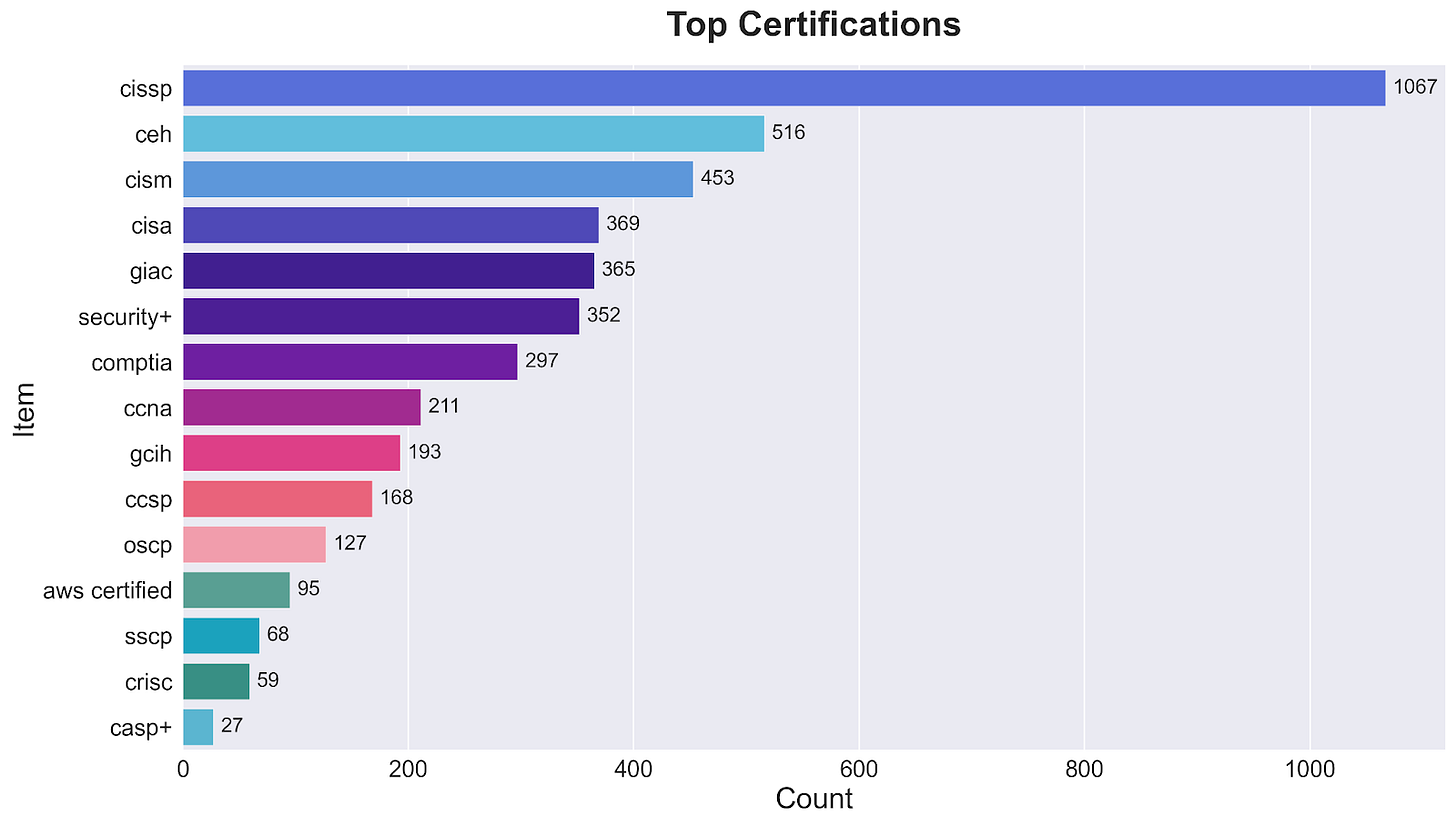
Analysis of 4,367 certification requirements reveals a clear hierarchy. CISSP dominates with 1,067 mentions, followed by CEH (516) and CISM (453). This distribution shows how security teams value broad security knowledge over specialized technical skills.
The certification requirements cluster in three tiers:
Top Tier (Governance-focused):
CISSP: 1,067 mentions
CISM: 453 mentions
CISA: 369 mentions
Middle Tier (Technical foundation):
Security+: 352 mentions
CCNA: 211 mentions
GCIH: 193 mentions
Specialized Tier:
CCSP (Cloud): 168 mentions
OSCP (Offensive): 127 mentions
AWS Certified: 95 mentions
Governance certifications (1,948 mentions) significantly outweigh purely technical certifications (785 mentions), suggesting organizations prioritize security management capabilities over technical specialization. This aligns with the earlier findings about compliance and risk management demands.
The Human Element: Beyond Technical Skills
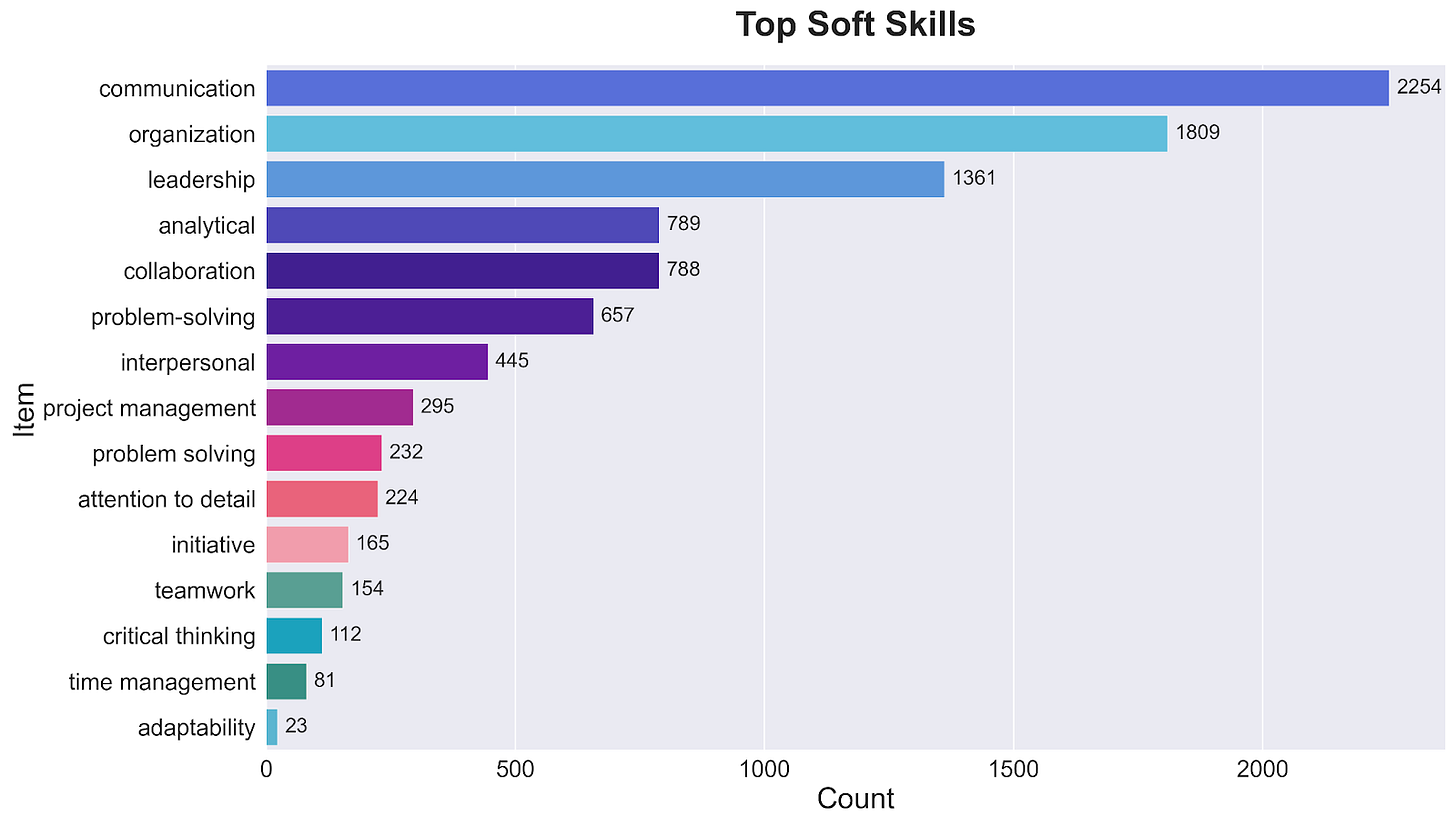
The soft skills requirements across security roles reveal an interesting hierarchy of what organizations value beyond technical capabilities.
Communication dominates with 2,254 mentions, followed closely by organizational skills (1,809) and leadership (1,361). This top tier suggests that managing security isn't just about technical solutions - it's about effectively conveying security needs and organizing responses across teams.
The middle tier focuses on problem management:
Analytical skills: 789 mentions
Collaboration: 788 mentions
Problem-solving: 657 mentions
Interpersonal skills: 445 mentions
Project execution skills form the foundation:
Project management: 295 mentions
Attention to detail: 224 mentions
Critical thinking: 112 mentions
Time management: 81 mentions
The high demand for communication and organizational skills, appearing more frequently than many technical requirements, suggests that security automation isn't reducing the need for human skills - it's shifting their focus from technical execution to program management.
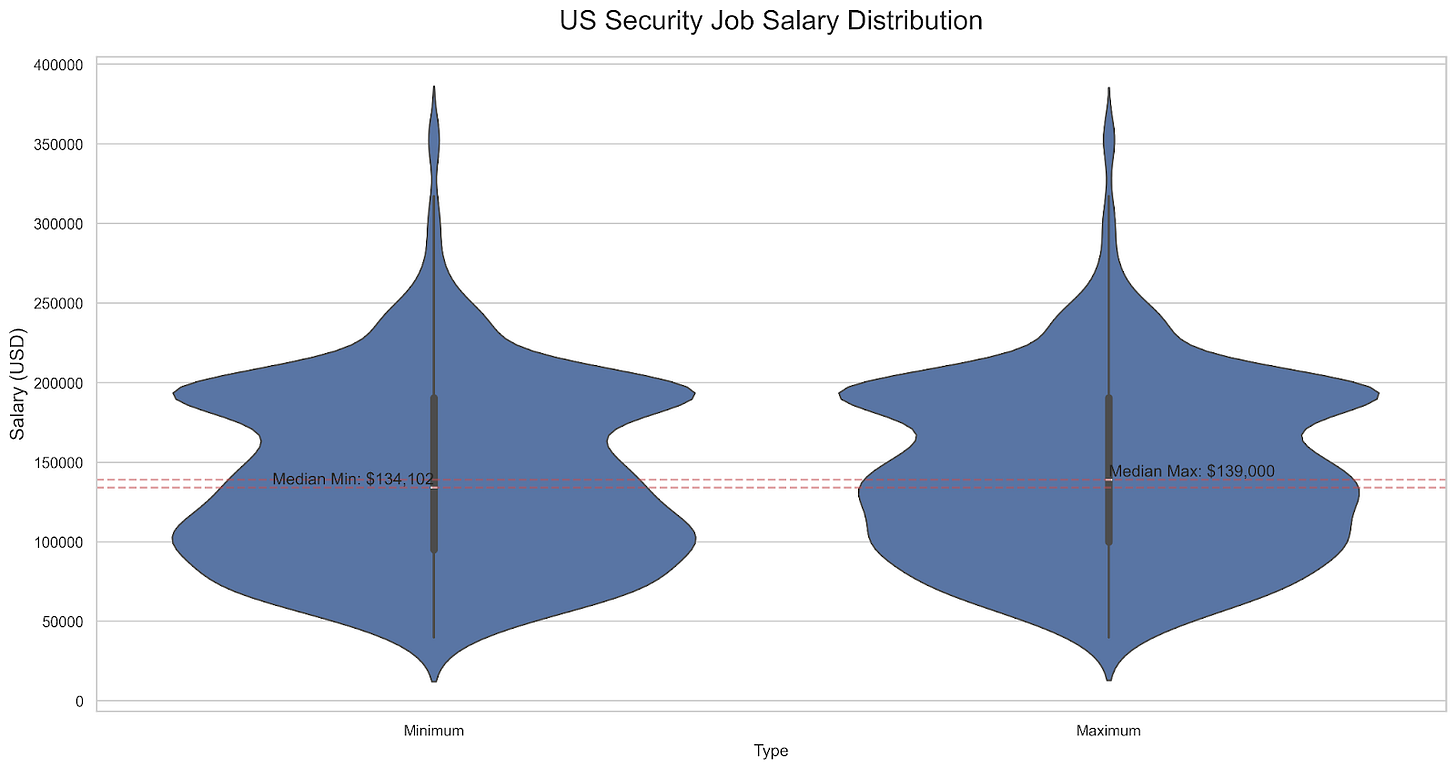
Show Me The Money: What Security Automation Pays
Analysis of 931 salary ranges reveals:
Median compensation ranges:
Base: $95,000
Ceiling: $144,031
Key breakpoints:
Entry level (25th percentile): $70,000 - $97,050
Mid-level (50th percentile): $95,000 - $144,031
Senior level (75th percentile): $105,000 - $190,300
Top-end roles reach significant premiums:
Maximum base: $600,000
Maximum ceiling: $1,400,000
The wide ranges, particularly at senior levels, suggest organizations heavily value professionals who can bridge technical automation with business needs. The substantial gap between median and maximum salaries indicates significant premiums for those who can handle complex automation and compliance requirements.
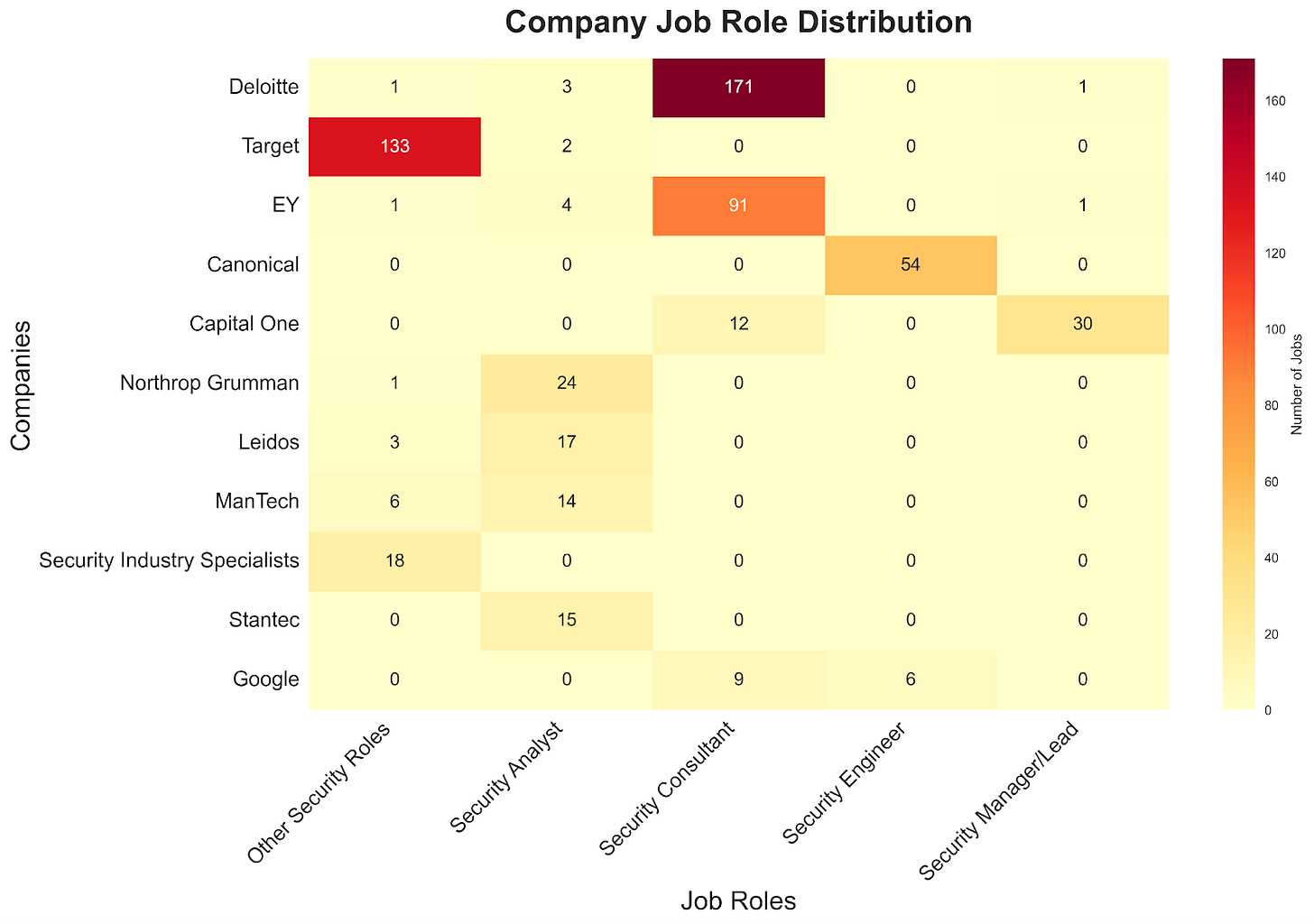
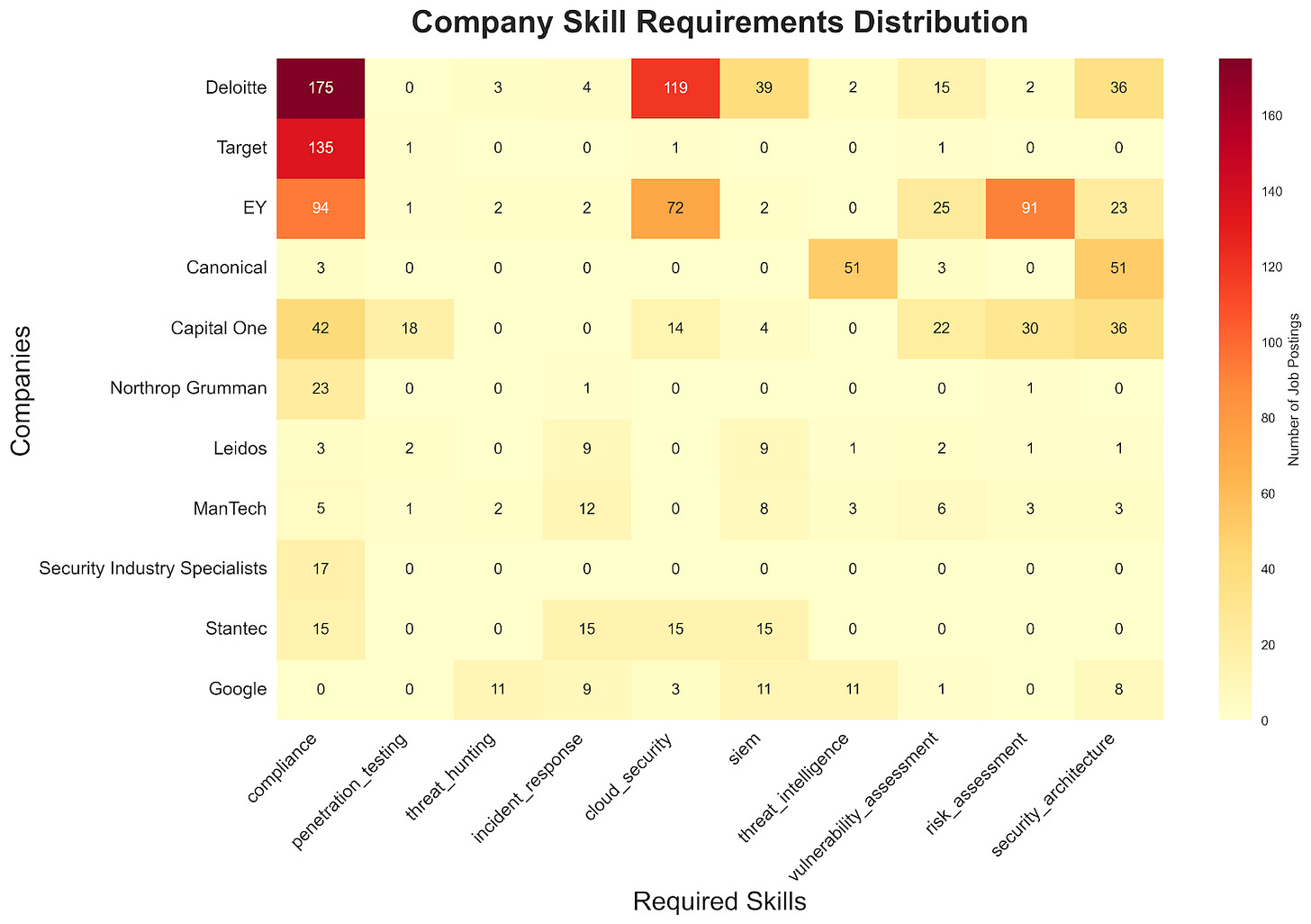
Security Teams: When Government Requirements Drive Commercial Security
The Government-Consulting Pipeline
Deloitte and EY's large security consultant numbers (171 and 91) reflect government/defense needs
Their heavy compliance focus (Deloitte: 175, EY: 94 mentions) aligns with federal requirements
Strong cloud security emphasis (Deloitte: 119, EY: 72 mentions) matches federal cloud initiatives
Architecture investment (Deloitte: 36, EY: 23) suggests building compliance-ready systems
This indicates consulting giants primarily extend federal security teams
The Direct Contractor Approach
Northrop Grumman, Leidos, and ManTech hire security analysts directly
Focus on incident response (ManTech: 12, Leidos: 9 mentions)
Strong SIEM and vulnerability assessment presence
Shows core security operations kept in-house while using consultants for scale
The Retail Response
Target's operational security focus (133 positions)
High compliance requirements (135 mentions) suggest regulatory pressure
Minimal investment in other areas shows compliance-first priority
Indicates regulatory requirements driving security structure
The Tech Sector Pattern
Canonical: Engineering-heavy (54 positions) with threat focus
Google: Balanced security approach across disciplines
Capital One: Management focus (30 positions) with broad skill mix
Shows private sector building security around business needs
Key Insights
Compliance shapes security organization:
Government contractors drive consulting demand
Federal requirements influence private sector approaches
Compliance dictates team structure and skills
Two distinct security models emerge:
Government-aligned: Heavy compliance, consultant-supported
Private sector: Business-driven, internally staffed
Consulting firms primarily serve as government security extension:
High compliance focus matches federal needs
Cloud security emphasis aligns with government modernization
Architecture investment supports regulatory requirements
This reveals government security requirements, filtered through consulting firms, shape much of enterprise security staffing. Organizations either align with these patterns or build distinct approaches based on business needs.
The Bottom Line: We Need Middle-Out, Not More Boxes
Remember our Silicon Valley reference? Just as Pied Piper realized compression needed a fundamental rethink with "middle-out," our analysis shows security automation needs its own paradigm shift. We're still making Box 3.0 when we need a completely new approach.
The data tells a clear story: security automation today focuses on building better tools rather than solving core security challenges. Despite a decade of "advanced" security automation and AI promises, organizations still desperately need professionals who can:
Navigate complex compliance requirements spanning multiple frameworks
Write custom code to make disparate security tools work together
Bridge the gap between automated alerts and business risks
Build documentation and evidence for audits
Manage security processes across teams and tools
The high demand for programming skills isn't a sign of digital transformation - it's evidence that current automation solutions are inadequate. While vendors promise no-code solutions, organizations are investing in developers because existing tools require extensive customization, integration, and maintenance.
We're stuck in a cycle of making incrementally better boxes:
Building faster alert systems when organizations need better compliance workflows
Creating more detection rules when they need better documentation processes
Automating the easy parts while the hard parts - compliance, risk management, process integration - remain largely unaddressed
The bear isn't just sticky with honey - it's stuck in a box of our own making. Our data suggests we need to fundamentally rethink security automation. Instead of adding more tools and automation layers to an already complex stack, we need solutions that address the actual challenges organizations face: managing compliance, documenting controls, coordinating responses, and providing evidence of security effectiveness.
Just as Pied Piper had to look beyond traditional compression approaches, security automation needs its own middle-out revolution - one that focuses on solving core security challenges rather than just making better tools.